Source: azure.microsoft.com
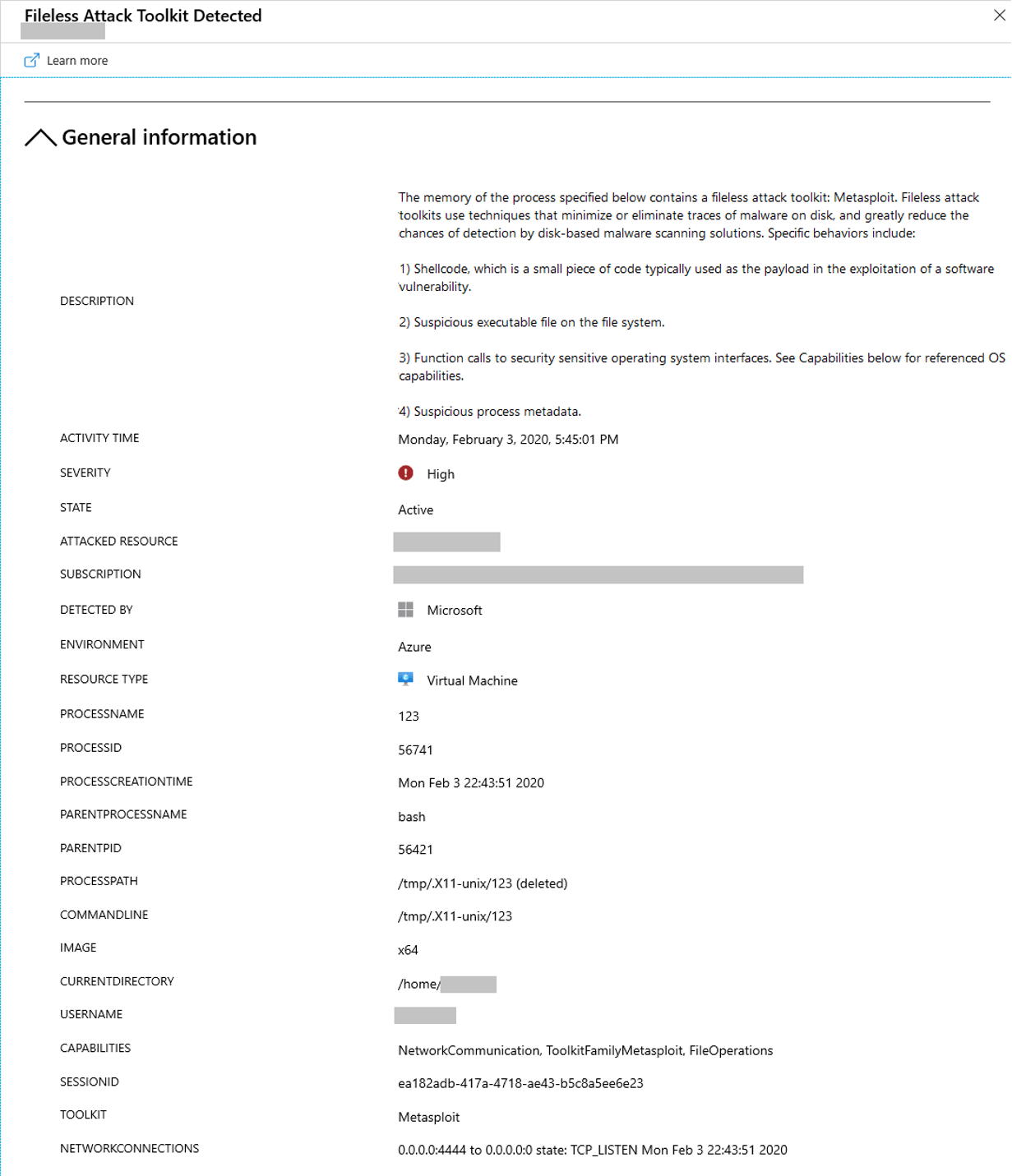
Fileless attack detection for Linux in previewCategory: Security, Data, Privacy
We think you might be interested in this job:
Prismatic
Related Articles
Community Partners
DevOps Careers