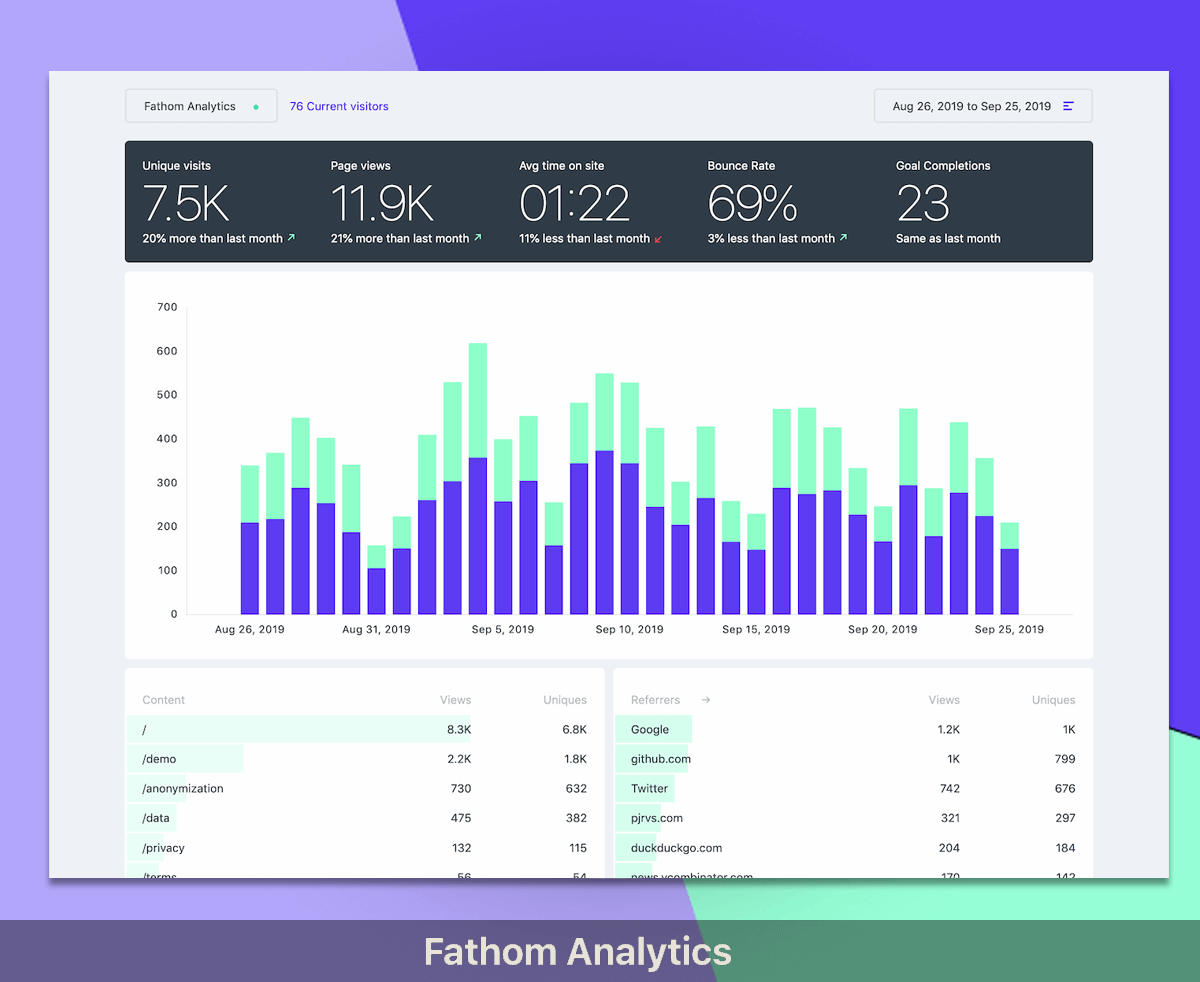
Latest DevOps Articles
Latest DevOps Articles curated daily from around the web.
Agile Methodology is a people-focused, results-focused approach to software development that respects our rapidly changing world. It works by first admitting th...
Software has been a crucial component to all of NASA’s major achievements, from space travel to the deepest images of our universe. Naturally, NASA’s need for h...
thenewstack.io
Magic-RegExp: A JavaScript Package for Regular Expressions
Much as I like https://thenewstack.io/taming-text-search-with-the-power-of-regular-expressions/ (or regex), part of their longevity is due to their separate dev...
thenewstack.io
How to Work with Containers in TrueNAS
TrueNAS is a https://thenewstack.io/truenas-scale-network-attached-storage-meets-high-demand/ you can deploy to your LAN or a third-party cloud host. But don’t...
unbiased-coder.com
Is Django Becoming Obsolete
I have used Django a lot over the years. I’d say I used it since inception but I missed the first few months of its announcement which had core changes and the...
thenewstack.io
The Move to Unsupervised Learning: Where We Are Today
Deep learning is a https://thenewstack.io/researchers-drop-the-zeroes-to-speed-deep-learning/ which particularly focuses on the class of algorithms that are ins...
thenewstack.io
3 Steps to Unlock the Power of Behavioral Data
The use of behavioral data to create the most descriptive views of a customer journey continues unabated. The most competitive organizations in every industry a...
thenewstack.io
From a Fan: On the Ascendance of PostgreSQL
The https://survey.stackoverflow.co/2022/#databases has been out for a couple of weeks now, and it’s jam-packed with good information to help end users and tech...
thenewstack.io
API Magic: Building Data Services with Apache Cassandra
All applications depend on data, yet application developers don’t like to think about databases. What if we could shift the balance, providing a data service in...
thenewstack.io
5 Quick Ways to Reduce Exposure and Secure Cloud Data
Switching to public cloud services is now a necessary strategy for most organizations’ long-term growth plans. But how do they adapt and expand their cybersecur...
thenewstack.io
Building Real-Time Location Intelligence Apps
Real-time location intelligence refers to the ability to gather, analyze and act on location-based data in real-time. Real-time location intelligence is used fo...
thenewstack.io
Can WebAssembly Solve Serverless’s Problems?
https://thenewstack.io/serverless/ computing continues to grow in demand for a range of use cases, for those organizations seeking to create and run application...
thenewstack.io
XSS Vulnerability Discovered in Backstage Software Catalog
https://backstage.io/ the open source internal developer portal created by https://thenewstack.io/how-spotlify-adopted-platform-engineering-culture/ has been ad...
On November 30, 2022, ChatGPT quaked the digital world, sending a tremor that even rattled the cybersecurity industry. Your https://www.upguard.com/blog/securit...
Nearlyhttps://www.globenewswire.com/en/news-release/2022/03/31/2413675/0/en/Largest-Healthcare-Data-Breaches-Reported-in-February-2022-Confirms-Need-for-Network...